Technical Risk Management
The possibility of changes that could have on a system, project, or entire infrastructure when an implementation does not work as anticipated comes under technical risk management.
And in case these failures won’t anticipated or managed this could result in degradation in performance, increased maintenance time, security breaches, system failures, and a significant amount of technical debt for your organization.
In order to ensure these technical risk management problems, you must have a reliable analysis solution. This will prevent greater damage to infrastructure or system problems. There are issues that could come up suddenly or immediately, so it is essential to be prepared.
Why Is Technical Risk Management Vital to Organizations?
One may ask why technical risk management is vital to organizations or whether are vulnerabilities silently waiting to bring down systems or cause security problems.
And to answer all these questions, is it better to have automated analysis solutions as these will help organizations to stay on top of these issues?
Technical risk control is the way of using methods and strategies to immediately identify existing or potential damages to a project. And to use automated analysis solutions to these technical risks will help in the early detection of these potential threats and damages. These can be used to figure out ways towards eliminating or decreasing the possible impact of Identified Threats.
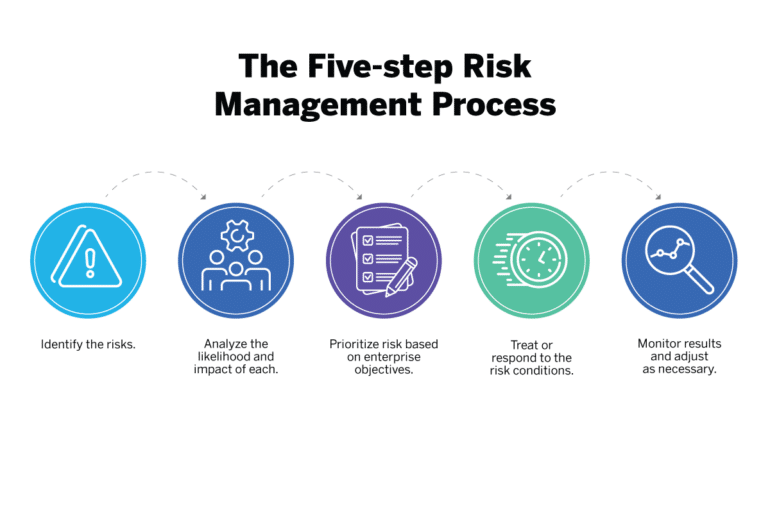
There are five essential steps of a risk management process.
- Identify the Risk
- Analyze the Risk
- Evaluate or Rank the Risk
- Treat the Risk
- Monitor and Review the Risk
Reduce Technical Risk through Automated Code Analysis
There are ways through which you can reduce technical risk. And in this article, we will talk about how to reduce technical risk through automated code analysis. Here, let’s start.
Automated code analysis might be used to detect potential threats based on size, number, complexity, and system vulnerabilities. You can use these pieces of information in various ways such as
- Increase Productivity
- Minimize Technical Debt
- Eliminate System Vulnerabilities
- Boost Code Quality
- Manage Complexity
- Minimize Software Risk
Automated code analysis using AIP makes sure that these issues are discovered early in the development life cycle and enables organizations to conduct improvement initiatives to prevent serious issues after a project is finished. Your firm will be able to improve code quality, eliminate system vulnerabilities, and significantly reduce development hazards by carrying out technical risk assessments using automated analysis at the code level.
What is Technology Risk?
Technology risk, also known as information technology risk, is any technological failure that has the potential to disrupt an organization. Data security breaches, cyberattacks, password theft, service disruptions, and many other technology hazards affect businesses.
Every sort of technological risk has the potential to result in financial, reputational, regulatory, or strategic risk if a proper incident response is not used. To anticipate issues in the future, an effective technology risk management strategy is therefore essential.
Types of technology risk
Due to modern technology, the risk of technology is much greater than we anticipate. Here are some common technology risks.
Data Breaches
Leaking or stealing of sensitive information by unintended parties is known as a data breach. There is more than one way through which it could happen such as external and internal factors.
External breaching means hacks, malware, or phishing scams. And by an internal factor, we mean improperly trained employees.
To prevent these breaching, a firm must do regular internal audits of IT environments.
Malware
Malware is a kind of software that causes harm to your devices. It is installed by an outsider to attack your system. There are many types of malware, but the two common ones are viruses and ransomware.
The Trojan Horse is a typical virus. Malware that imitates a legitimate program can be installed and then used to carry out the attacker’s objectives, such as data theft, activity monitoring, or gaining access through a backdoor to secure systems.
Ransomware is a type of malware that prevents a user from using their computer until the attacker’s demands are met (typically by paying a ransom or releasing confidential information).
Dated apparatus
To keep software up to date, enabling routine or automated downloads from the program provider is frequently all that is required. These updates include patches to protect your sensitive data from new and existing cyber threats.
Conclusion
When starting a business, you will face many difficulties such as technical risks or technology risks. And to fix these problems, you need expert protection. And here, you will get our professional help in reducing these risks. You need a proper strategy to tackle these risks that could affect your success. So, come on board with us, and let’s sail smoothly and achieve our common goals.
